Published by on

The mobile technology wonderful but vulnerable to abuse in ways that can cause terrible consequences: face recognition, voice recognition, interactive real-time ..
Mobile technology is booming with new services and applications are constantly appearing to help users stay connected, updated information, increase productivity and entertainment. However, as modern technology will go hand in hand with greater risk. A number of utilities that can be exploited fraudulent purposes, tracking or exploit victims. Below, we listed five such technologies:
1. GPS

In 2011, two major shopping centers in the U.S. has been outcry when it announced plans to discreetly monitor customers through mobile devices to their personal. Purpose for which the shopping center is given as to monitor the flow of people into viewing booth, helping retailers improve the layout display of goods. This project was shut down after being accused of violating the privacy of our customers.
GPS tracking technology is useful in that it provides detailed information and accurate anonymous traffic but people can move to improve the layout of the museums, stadiums, roads etc. However, it is scary when a company can anonymously track you based on personal devices, which can even collect identifying information easily stolen or traded.
2. Subscribe to user environment

March past, Google has patented technology capable of determining not only the user's location, but also know what they are doing based on sound, temperature and other factors of the environment where they stand.
For example, when you call the 411 service from Google - Google's phone service allows users to search for a product to sell in the cities of America or Canada - from a stadium, Google will be based on the sound of the crowd to realize you are watching a basketball game. From there, they will send you an ad inappropriate, the coupon can be served dinner at a restaurant near the stadium, a thin coat at a nearby store if the evening temperature low.
Environmental monitoring technology has clear utility mentioned above, but also a threat when it reveals too much information about the user.
3. Voice recognition technology and user mood

03/2012, Fujitsu and Nagoya University in Japan have announced a technology capable of "reading" is the desired state and certain of the user. In particular, this technology aims to detect fraudulent behavior over the phone by filtering out the keywords that perpetrators use, measured voice and high voice of the victim. If the result reached alarming levels, the victim will be warned about the risk of fraud.
Using voice technology to prevent crime is a good purpose. However, imagine if this technology becomes popular, a criminal can track your mood from his phone, as well as seeking to change the tone and pitch voice, what would happen?
4. Face

Many companies have sought to develop facial recognition software unreliable. For example, use Facebook features face detection to identify your friends in a picture. Most recently, a company called Face.me announced through which technology, you just need a camera, the software will only take about 1 second to confirm the identity of that person, then you can connect with them through social networks like Facebook, Twitter and LinkedIn.
If used safely and carefully, face recognition technology is very useful. However, being able to identify and connect with a person just by taking pictures of people that can obviously lead to more harassment predictable.
5. Real-time Interaction (Augmented Reality)
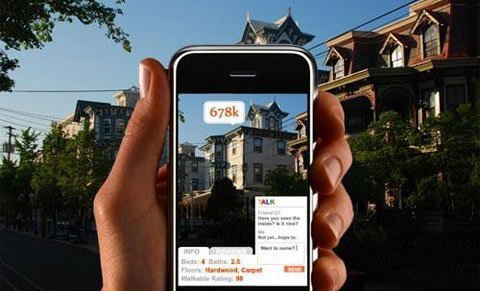
He idea behind the technology interact in real time as you just point the device has an integrated camera at an object, you will immediately receive information about that object. For example, the application of Autonomy Aurasma, you can aim the camera on a still photo taken a sports event, the device determines that the scene and start playing a video clip on sports events there. Meanwhile, there are reports that the upcoming Google Google Glass - equipment that allows users to look at a street and on the glass screen will display the digital information on that street (name of child City, the surrounding landscapes, the way ..)
Real-time interactive applications bring great for entertainment, education and business. However, it is extremely dangerous if the thief can take advantage of this technology to "see through" real time is where you are, do anything, with anyone ..
(According ICTnews / PCWorld)
